Security of mobile apps is the key to their success on the market. However, protecting information, transmitting data over the network, and accounting for hidden features are often challenging, and, unfortunately, fraudsters can take advantage of vulnerabilities of your app. According to McAfee and the Center for Strategic and International Studies, the global economy lost more than a trillion dollars in 2020 due to hacker attacks. And fraudulent methods are becoming more inventive every year. This imposes additional responsibility on the developers of mobile apps. So, in this article, we’ll tell you about common mobile security threats and the best security features for mobile apps to help you create a secure and high-quality application for your business.
Table of contents:
- Common mobile security threats
- The best practices to improve mobile app security
2.1 Secured code
2.2 High-level authentication
2.3 Reliable data storage
2.4 Data encryption
2.5 Secure communication
2.6 Testing - Final thoughts
Common mobile security threats
It is difficult to imagine our lives without mobile apps today. According to DataReportal, the average user spends 6 hours and 43 minutes online. Moreover, 10 out of every 11 minutes users spend using mobile devices. What’s more, 44% of apps contain personal data that requires a high level of security, and 66% of apps have functionality that could compromise user privacy.
Among the leading mobile apps with more than 500,000 downloads, 94% contain at least three medium-risk vulnerabilities, and 77% contain at least two critical vulnerabilities, according to the Beta News survey. And about 1/3 of the apps contain hidden functionality and bottlenecks in the source code. If you want to develop a secure and feature-rich mobile app, you should check out our guide to mobile app development.
The first step in creating a secure mobile application is to be aware of the basic methods of attacks on mobile devices. To do this, industry experts put together a developer help called the Open Web Application Security Project (OWASP). It includes the OWASP Mobile Top 10 listing the main threats to mobile security. According to this list, among the main security threats are improper platform usage, insecure data storage, insecure communication, insecure authentication, and insufficient cryptography.
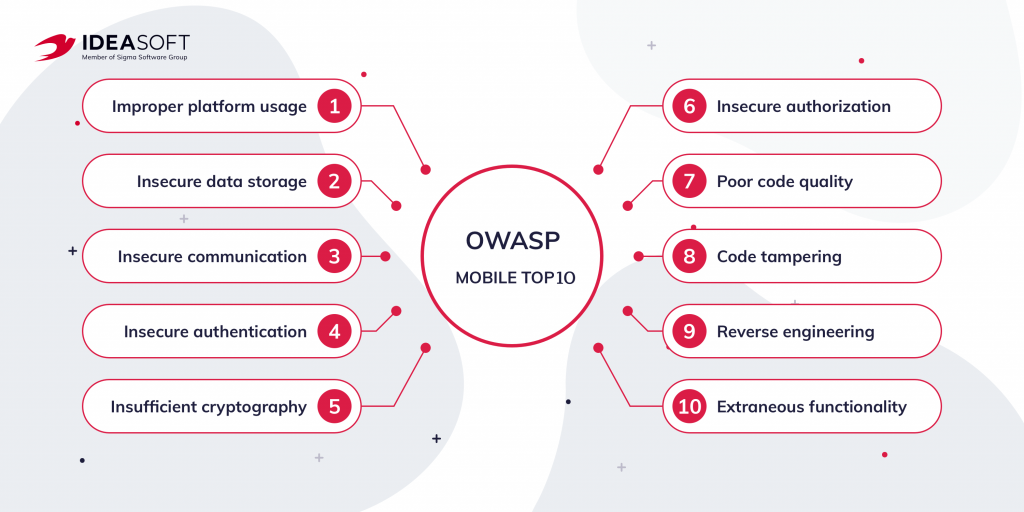
You should keep in mind that users know that the number of online threats is increasing. So they often try to find out what are some must-have’ security features for mobile apps, because they want to use only reliable applications. That’s why when developing an app you should make sure that your software product meets both security standards and the expectations of your users.
The best practices to improve mobile app security
Answering the question of how to make a mobile app more secure, first of all, you should know mobile app development trends to keep abreast of the latest tendencies in the development world. Secondly, there are many different ways to improve security, depending on the type of application. Also, the implementation of some of them depends on the development team’s experience. Newbie developers, for example, will not be able to provide reliable data encryption. Here are some tips on how to ensure mobile app security.
Secured code
Often developers turn to third-party libraries to simplify the development process. This is a common and effective practice. However the problem is that not all developers care about security, and often third-party libraries have bugs that affect the reliability of the entire system. Consequently, if programmers are borrowing an implementation from outside, they must be sure that it will not make the system more vulnerable. To avoid poor coding issues, developers should spend more time analyzing and testing it. Here are some of the best practices for keeping your code secure:
- Use third-party static analysis tools to detect memory leaks and buffer overflows.
- Avoid simple logic in your code known to hackers.
- Use the latest updated versions of third-party libraries for development.
- Validate input from all untrusted data sources.
- Use testing best practices including fuzz testing, penetration testing, and source code audits.
- Conduct code reviews regularly.
Secure code can stop attackers from successfully hacking an application. Be sure to check your code for vulnerabilities and bugs. Use code hardening and code signing. Work only with safe, proven tools and try to make the system flexible enough so that in case of updates everything goes quickly and smoothly. Remember that secure code is one of the best security features for mobile apps.
High-level authentication
The most common application vulnerabilities in 2019 were related to improper security configuration. But the highest risk was associated with weak authentication. Such a problem was found in 45% of the examined applications. An unlimited number of attempts to log in to the account is a great threat. Password-only authentication is the factor that contributes to the largest number of attacks through brute-force login/password combinations. So password complexity requirements, which used to be the gold standard, now undermine security. Therefore, according to NIST recommendations, organizations should switch to multi-factor authentication if they haven’t already done so.
Here are more tips to ensure secure authentification:
- Ensure that passwords and security keys are not stored locally on the mobile device.
- Enforce periodic authentication of user credentials and logouts from the server-side.
- If you are using local data storage, make sure it is encrypted with an encrypted key obtained from the user’s credentials. This forces the app to authenticate the application data at least once.
- Don’t allow loading app data if the server has not authenticated the user’s session.
- Limit the number of login attempts and password reset requests for every account and IP address range.
User registration and authentication system is a critical element of service security. In most cases, you’re better off not making it from scratch, much less using a password as an authentication factor. It is better to delegate the entire function to a third-party service, such as a popular social network, etc.
Reliable data storage
First of all, you should not store sensitive data in local storage, as there is an increased risk of attack. If you still need to do this, take care of data encryption so that in the case of a leak, attackers cannot read the information and compromise users. The very first targets on a cracked device for scammers are SQL, log files, XML data stores, binary data stores, cookie stores, etc. Make sure your application is not vulnerable to these threats, and also follow the next tips:
- Make sure the server and app authenticate each other before exchanging data.
- Encrypt files and networking communications.
- Adapt your code to different mobile platforms as different platforms have different security features.
Also, both iOS and Android provide security guides to developers. Make sure your development team is ready to follow them and has the necessary expertise to implement the best security features for mobile apps as suggested in these guides.
Data encryption
Data encryption is one of the most important steps in building a secure mobile app. Deficiencies in cryptography and outdated encryption methods can make your app an easy target for attackers and leak sensitive user data. Encryption algorithms convert plaintext data into ciphertext, hiding the original content. There are several encryption methods. It can be symmetric (secret-key encryption) which uses a single cryptographic key to encrypt and decrypt data or asymmetric (public-key encryption) which includes several keys for encrypting and decrypting data, which are mathematically related to each other.
Both iOS and Android have encryption features to protect user data. The challenge for developers is to use best practices for these mobile platforms, in particular, to ensure that encryption keys are securely protected and cannot fall into the hands of fraudsters. For example, developers should never place encryption keys in the same directories as encrypted data. Also, the best encryption methods include public-key encryption algorithms, hashing, Message Authentication Codes, signatures, key derivation functions.
Secure communication
Insecure use of interprocess communication is a common critical vulnerability that can lead to data theft as it travels over the network. The fact is that mobile applications, as a rule, exchange data according to the client-server model. The client-side of the app is the program that users install on their mobile devices. However, this application interacts with the back-end. This part is responsible for processing and storing information, as well as synchronizing user data between devices. Therefore, the transmission process through the operator’s network or the Internet must be implemented securely in order to avoid interception of traffic from proxy servers, base stations, etc.
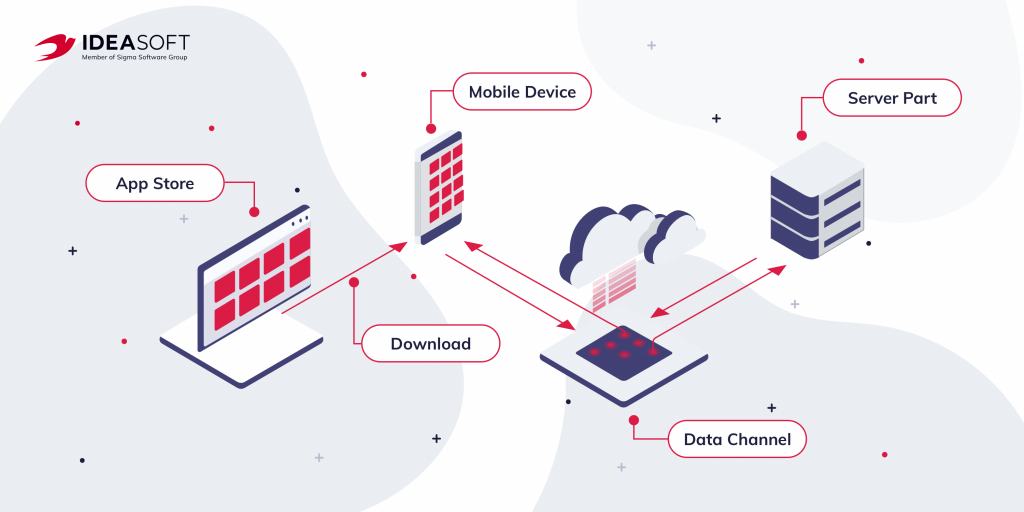
To ensure secure communication, mobile app developers must use industry-approved encryption protocols and other practices, including installing SSL/TLS certificates from trusted certification authorities and alerting users when an invalid certificate is found. You also need to establish a secure connection only after the endpoint server has authenticated with trusted certificates in the keychain. Make sure your development team doesn’t neglect best practices for secure communication and conducts sufficient testing to ensure that there are no system vulnerabilities.
Testing
You should keep in mind that it is not enough to be concerned about the safety of mobile applications at the end of the life cycle, since it is much more expensive to fix bugs in the last stages of project development. A robust early testing strategy of mobile apps can help avoid future security problems. Therefore, it is important to implement testing at all stages of mobile app development in order not to accumulate bugs. This is not actually a security feature, but we can’t fail to mention this. If you want to create a truly secure app, you need to test it over and over again. Only this can show how effectively other security features have been implemented.
Mobile app security testing is aimed at identifying the risks and weaknesses of the system. To do this, QA specialists create test cases based on the main threats and make sure that the system can resist them. This includes vulnerability analysis, web service security testing, client security testing, AI testing tools, and the like. In addition, certain platform-related tests can be carried out, since native applications, for example, are created using OS features. In any case, your project needs a team of experienced testers who will be able to assess the security of your app. So don’t neglect this step.
Final thoughts
Now you know the best security features for mobile apps and how important it is to work with an experienced development team. Securing a mobile app is a challenging and demanding task that your team must take seriously. Unfortunately, attackers are becoming more and more inventive and it is no longer enough to inject a few security features into an app. Each project implies its own data protection scenarios and has its own characteristics. That’s why the best way to create a secure mobile app is to contact experienced specialists. They can assess all the risks and develop an effective security strategy.
An experienced mobile development team of IdeaSoft will be happy to help you develop a feature-rich and secure mobile app. We provide a full cycle of software development services from business analysis and UX/UI design, to programming, testing, and support. Check out our delivered projects and feel free to contact us directly.

