Money laundering is a big issue today. United Nations Office on Drugs and Crime states that money laundered globally exceeds 2-5% of the global GDP. It is approximately $800 billion to $2 trillion in just one year. To combat money laundering, financial institutions introduce Know Your Customer (KYC) and Know Your Transaction (KYT) compliance measures.
Looking for KYC or KYT experts?
Our experienced team is well-versed in all the nuances. We can provide invaluable insights to help navigate the KYC and KYT in fintech as well as crypto. Feel free to book a consultation right now!
At IdeaSoft, we worked a lot with Web3 and fintech projects and have often dealt with KYC and KYT. Our case studies demonstrate our vast expertise in a variety of industries. This is why we aim to shed light on KYC vs KYT. This article will discuss KYT and KYC in finance security as well as why financial institutions should use KYT.
Table of Content:
- Comparing two approaches: KYT vs. KYC
- Know Your Customer (KYC)
- Know Your Transaction (KYT)
- KYT and KYC in the Financial Sector
- Why Should Financial Institutions Use KYT?
- Summary
Comparing two approaches: KYT vs. KYC
KYT and KYC are two compliance measures that are often confused. We have created a comparison table of KYC vs. KYT to help you better understand these terms.
| KYT (Know Your Transaction) | KYC (Know Your Customer) | |
| Purpose | To verify the legitimacy of individual financial transactions. | To verify the identity and background of customers or clients. |
| Scope | Focuses on individual financial transactions, examining the source of funds and destination. | Focuses on verifying the identity, address, and financial history of individuals or legal entities. |
| Applicability | Typically used by financial institutions, cryptocurrency exchanges, and payment processors. | Used by various organizations, including banks, insurance companies, and other entities offering financial services. |
| Timing | Applied in real-time or near real-time to monitor and flag suspicious transactions. | Conducted during the onboarding process and periodically updated. |
| Data Collected | Transaction-related data such as sender, receiver, amount, date, and purpose. | Personal information, identification documents, and financial records of customers. |
| Regulatory Basis | Often required to comply with anti-money laundering (AML) and counter-terrorism financing (CTF) regulations. | Required to comply with AML and CTF regulations and other financial regulations depending on the jurisdiction. |
| Risk Mitigation | Helps in identifying and preventing illicit transactions and suspicious activities. | Aims to prevent identity theft, fraud, and ensure that customers are not involved in illegal activities. |
| Customer Interaction | Typically less intrusive for customers, as it primarily involves monitoring transactions. | Requires more interaction with customers during onboarding and periodic reviews. |
| Key Challenges | Analyzing a large volume of transactions in real-time to detect suspicious patterns. | Ensuring the accuracy of customer information, addressing fraud attempts, and keeping customer data secure. |
KYT (Know Your Transaction) and KYC (Know Your Customer) are both critical compliance measures used in the financial industry to prevent money laundering, fraud, and other illicit activities. Let`s discuss them in more detail.
Know Your Customer (KYC)
Know Your Customer (KYC) is a customer identity verification process that financial companies use to collect customer information. It includes their identity, financial condition, and other information that may be relevant to possible financial risks.
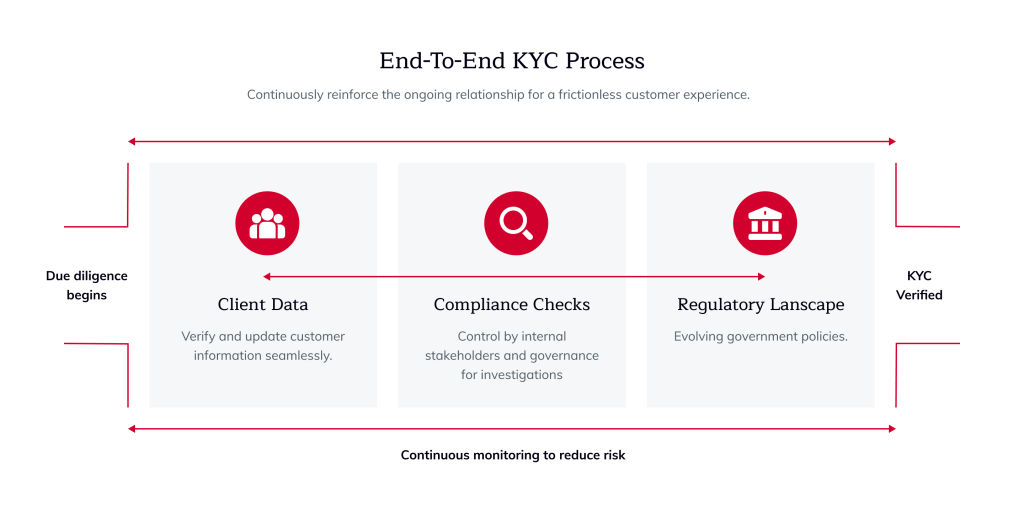
KYC verifies customer identity and is part of a triad of financial and cybersecurity protocols. It is used in different areas: finance, e-commerce, online payments, and insurance.
KYC in crypto
KYC is the basis for transactions on most crypto exchanges. In the cryptocurrency industry, KYC is used to verify customers’ identity, location, and financials. This allows platforms to use the information obtained for user and fraud protection and to prevent money laundering.
KYC on cryptocurrency exchanges and exchanges is also a prerequisite for accessing products and services. It is possible to use the services without KYC but with certain limits.
In addition, KYC can be used to verify customers who want to use an exchange to store their digital assets. In this case, two-factor authentication (2FA) is required to protect the client’s account.
Know Your Transaction (KYT)
Know Your Transaction (KYT) is an addition to KYC. Its primary goal is to prevent money laundering, terrorist financing, and other criminal activities by detecting unusual or suspicious transaction patterns. By analyzing real-time transaction data, businesses can quickly identify potential risks and take appropriate action.
KYT is typically implemented as a software solution that integrates with an enterprise’s existing financial systems. The software uses machine learning and other advanced techniques to identify patterns in transaction data.
What are the disadvantages of KYT?
KYT is a powerful tool for managing the risks associated with financial transactions. It can help businesses comply with regulatory requirements, reduce the threat of fraud and other illegal activities, and improve the efficiency of their financial systems.
However, Know Your Transaction limitations have an impact on this technology:
- False positives. One of the biggest problems with KYT is the risk of false positives, which can occur when the system flags a transaction as suspicious even though it is not. This can cause unnecessary delays and additional costs to the business and involve image threats.
- Complexity. Implementing a KYT solution can be complex and time-consuming, requiring companies to invest in new technology and hire additional technical staff to manage the system.
- Confidentiality. KYT solutions can raise privacy concerns among users, especially in the crypto industry, where anonymity is valued. Users may hesitate to use a service that tracks their transactions and stores their personal information.
- Cost-effectiveness. Implementing KYT can be costly, especially for small businesses that may not have the resources to invest in new technology and personnel.
These issues must be carefully addressed to ensure that the benefits of KYT are realized while minimizing potential drawbacks.
KYT and KYC in the Financial Sector
KYC is widely used in banking, international trade, online payments (e.g., PayPal), insurance companies, securities exchanges, and crypto exchanges (Binance, Coinbase, Huobi, etc.). The purpose of KYC is to help companies collect information about customers to protect them from financial fraudsters and prevent money laundering and terrorist financing in the first place.
KYT is also used in various industries, including banking, finance, and e-commerce. Any business that deals with financial transactions can benefit from KYT as it helps identify and manage the potential risks associated with these transactions.
In banking and finance, KYT is used to comply with anti-money laundering regulations that require organizations to track and report suspicious transactions.
Need more financial details?
Let us help you, and correctly draw up the requirements for your project
In e-commerce, KYT is used to prevent fraud and other illegal activities. By analyzing transaction data, online retailers can identify potential scams and take appropriate action, such as canceling orders or freezing accounts.
In crypto, KYT solutions can identify potential threats and alert crypto exchanges to take appropriate action. KYT has become an important tool for risk management in the crypto industry. This is because the decentralized and anonymous nature of many cryptocurrencies has also made them a target for criminal activities.
For example, KYT solutions can identify transaction patterns that are inconsistent with typical user behavior, which could indicate criminal activity. They can also flag transactions involving known criminal organizations or countries under sanctions. KYT can also help crypto businesses better comply with government regulations, reducing the risk of fines.
Why Should Financial Institutions Use KYT?
Here are 5 primary reasons why KYT in fintech is important:
- Compliance with regulations. Financial institutions must adhere to Anti-Money Laundering (AML) and Counter-Terrorism Financing (CTF) regulations. Know Your Transaction (KYT) is an indispensable tool for institutions to fulfill these obligations, ensuring their full compliance and steering clear of potential penalties for non-compliance.
- Detection and prevention of financial crime. KYT empowers financial institutions to swiftly identify and thwart fraudulent or criminal activities, including money laundering, terrorist financing, and other illicit financial schemes. This robust system not only safeguards the institution but also shields its customers from financial losses and the tarnishing of its reputation.
- Risk management. KYT emerges as a crucial asset for financial institutions in their risk management strategies, enabling them to pinpoint and effectively mitigate risks associated with specific transactions, customers, or counterparties.
- Enhanced customer due diligence. KYT elevates the precision and depth of customer due diligence processes for financial institutions by providing comprehensive insights into a customer’s transaction history and potential risks intertwined with their financial activities.
- Elevated operational efficiency. KYT’s integration into financial institutions’ operations leads to substantial enhancements in operational efficiency. It streamlines the monitoring and tracking of transactions, diminishing the need for labor-intensive manual processes and enhancing accuracy.
As a part of IdeaSoft venture builder, our leaderboard developed the idea and co-founded GlobalLedger protocol. This innovative startup provides indispensable solutions to banks, fintech companies, and crypto startups, ensuring their strict adherence to mandatory anti-money laundering (AML) regulations in the crypto asset domain.
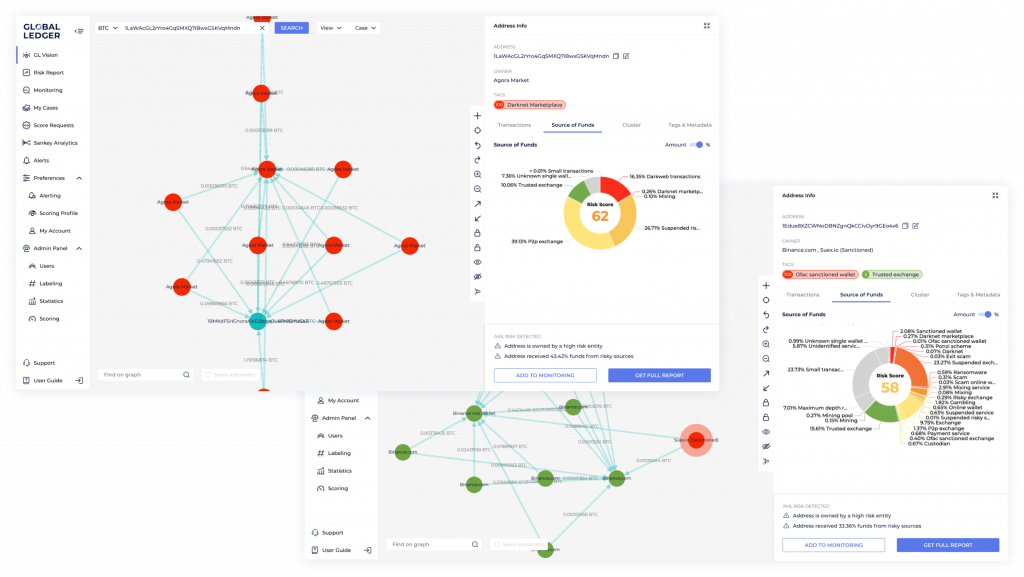
With the utilization of GlobalLedger technologies, regulators and law enforcement agencies are able to effectively supervise financial institutions in accordance with the law guidelines set by the Financial Action Task Force (FATF). By introducing such innovative tools, GlobalLedger plays a crucial role in promoting transparency, security, and regulatory compliance within the rapidly evolving landscape of cryptocurrencies.
Summary
It makes no sense to choose KYC or KYT. In practice, these two processes go hand in hand, with KYC providing the groundwork for KYT to operate effectively. The synergy between them enhances the overall security and integrity of financial systems and reduces the risk of criminal activities.