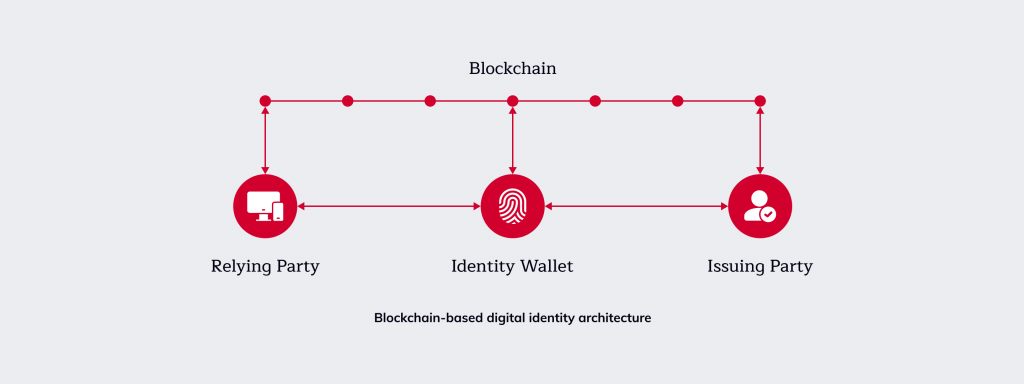
Today, businesses are getting more interested in developing blockchain-based identity management systems. This is because our digital identity plays a crucial role in digital transactions. According to the Digital Payments Global Market Report 2023, the digital payments market will grow to $197.87 billion in 2027 at a CAGR of 15.5%. This means that people will make even more transactions using their data.
At IdeaSoft, we know how to integrate blockchain in the finance app. This is why we aim to shed light on this subject and delve into its critical aspects. This article will discuss the benefits of blockchain for identity management, digital ID limitations, and how to develop a blockchain-based identity management system.
Are you ready to be at the forefront of this digital revolution?
Contact us at IdeaSoft right now! Together, we will build a future where secure, user-centric, and efficient digital identities become the new norm.
Table of content:
- What Is Digital Identity?
- Digital ID Limitations
- Benefits of Blockchain Identity Management Solutions
- Developing a Blockchain-Based ID: Main Steps
- Summary
What Is Digital Identity?
Digital identity serves as a virtual representation of your personal information. It is the key to verifying your online presence. Virtual identity empowers you to confirm your authenticity when logging into your email account or conducting secure online transactions without presenting physical identity documents such as a passport or credit card.
Digital Identity Solution Market size was valued at USD 25.2 billion in 2022 and is anticipated to register at a CAGR of 16% between 2023 and 2032. The rising workforces and connected networking devices are propelling the demand for digital identity solutions that offer better security to organizations.
Nevertheless, data breaches remain one of the most significant issues for digital identity solutions. This is why modern technology companies strive to solve this problem by managing identities with blockchain technology. This technology can transparently protect data from fraudsters. And this is what we are going to discuss further in this article.
Digital ID Limitations
Digital identity development limitations can present hurdles even with innovative blockchain technology. While identity management with blockchain can revolutionize this domain, several challenges and obstacles still must be addressed to fully realize its potential.
Current digital ID limitations:
- Regulations. European digital identity faces legislation, such as GDPR, that imposes strict regulations on the form and types of data storage. For instance, sensitive data like passports, medical records, and tax identification numbers cannot coexist in a single resource with unified access, as it poses a significant risk in a data breach. Consequently, the most successful digital identity solutions development often occurs in emerging countries with less stringent governmental restrictions on personal data storage and transmission, such as Ukraine, or in regions like Asia (e.g., UAE).
- Emerging technology. Despite a decade of discussions about implementing digital identity, there are still limited global use cases, and their implementation remains challenging. This is especially true for blockchain-based solutions, which were hampered until recently due to the public accessibility of all data stored in public blockchains. Additionally, creating something entirely new and unprecedented in the world presents inherent challenges, as the potential implications and difficulties during development are often unclear.
- Entity definition. Determining who manages the data and balancing restricted access with comprehensive access control can be complex. Finding a way to redefine how data is collected and accessed, especially in a blockchain context, is a significant challenge that needs innovative solutions.
The development of the digital identity sector is undeniable. Currently, digital identity solutions in the USA and Europe are represented by private corporations, including young startups. They are actively working on their own initiatives to achieve technological breakthroughs. Some of them have already succeeded as they see a lot of advantages.
Andrei Lazorenko, CEO at IdeaSoft
Benefits of Blockchain Identity Management Solutions
Here are the main benefits of blockchain-based identity management systems:
- Cost savings. Companies won’t need entire compliance departments to enter and verify data. This operational workload is reduced.
- Time efficiency. Registration processes everywhere will become quicker and less prone to human error, saving time spent on data processing.
- User convenience. In Europe or America, bank registration can take weeks, involving document verification and background checks, especially for foreign citizens. This causes delays of months. Digital identity can alleviate this inconvenience, enabling near-instant registration at lower levels and faster processing for high-level data access.
- Security and transparency. All data will be accessible within a single system, significantly reducing fraud and deception at all levels, from enrolling a child in daycare to identity theft.
Many financial institutions, including central banks, will soon need to embrace market conditions and adopt digital identity for user verification and account opening. Therefore, many must consider implementing blockchain for identity verification and its potential benefits for their businesses right now.
Developing a Blockchain-Based Identity Management System: Main Steps
Now, let`s discuss how to create a blockchain-based identity verification system in 5 steps.
Project Scoping and Stakeholder Expectation Management
The first step in a blockchain-based identity management system development is to identify the target audience. Understanding who will use the system and benefit from it is vital. Typically, the target audience includes:
- Individual users. These people will use the system for secure access to services, digital documents, and transactions.
- Businesses. Organizations that may want to integrate the system for employee authentication, customer onboarding, and secure data sharing.
- Government agencies. Entities looking to enhance citizen services, streamline identity verification, and protect sensitive data.
Next, you must outline the specific features and functionality required for your blockchain identity solution. These features may include:
- Decentralized identity verification. Using blockchain to securely verify and validate user identities without a central authority is important.
- Self-sovereign identity. You should empower users to have control over their identity information, granting access as needed.
- Privacy and security. Implementing robust encryption and cybersecurity measures to safeguard user data is a must.
- Interoperability. You should ensure the system can seamlessly integrate with existing platforms and services.
In any project, it is also necessary to clearly define the roles and responsibilities of stakeholders.
Got lost in tech details?
Let us help you figure it out, and correctly draw up the requirements for your project
Choosing the Right Blockchain Platform
When it comes to blockchain identity management, it’s crucial to select the most suitable platform to meet your needs. In the current landscape, one of the most effective methods for achieving this is utilizing public blockchain shard chains.
Here are a few successful blockchain development platforms based on which you can develop blockchain-based identity apps.
Polygon Supernets
Polygon Supernets are application-specific chains operating on the Polygon Edge consensus client with PolyBFT consensus. These networks enhance data storage, processing power, and transaction capabilities through scaling solutions, including layer-2 techniques, parallelization, and ZK technology.
Avalanche Subnet
Avalanche Subnet is an independent and sovereign network within the Avalanche ecosystem that defines its own rules regarding membership, token economics, and consensus mechanisms. Subnets consist of a dynamic group of Avalanche validators collaborating to achieve consensus on the state of one or more blockchains. A single Subnet validates each blockchain, but a Subnet can validate multiple blockchains.
Avalanche’s Primary Network is a unique Subnet comprising three coexisting blockchains: the Platform Chain (P-Chain), the Contract Chain (C-Chain), and the Exchange Chain (X-Chain). Importantly, every validator in a Subnet must also validate the Primary Network.
NEAR Nightshade
NEAR Nightshade is a developer-friendly blockchain designed for scalability and decentralization. It employs “sharding” technology to ensure high-speed and low-cost transactions, addressing common issues like network congestion and high fees. It processes approximately 1.3 million daily transactions with near-instant finality.
Designing the Identity Management System
The design phase is critical to ensure a robust, secure, and user-friendly blockchain-based digital identity system. The user interface should feature:
- Simplicity. Ensure a clean, easy-to-navigate design that accommodates users of all technical backgrounds.
- User control. Empower users to manage their identity easily, including adding, updating, or removing information.
- Accessibility. Ensure the system is accessible to individuals with disabilities, adhering to inclusive design principles.
- Multi-platform compatibility. Develop a responsive design that functions seamlessly on various devices and browsers.
User experience should be prioritized:
- Onboarding guidance. Create clear instructions for users to create and manage their digital identity.
- Feedback and notifications. Provide real-time feedback during processes like identity creation and notify users of important actions.
- Security awareness. Educate users about the security features in place and best practices for protecting their digital identity.
A secure authentication and authorization process is also paramount. Key elements include multi-factor authentication (MFA), token-based authorization, role-based access control (RBAC), and audit trails.
Testing and Deployment
After designing a robust blockchain-based identity management system, the next crucial steps involve thorough testing in a staging environment and secure deployment to production.
Testing in a staging environment is essential to identify and address potential issues before deploying the system to production. The following types of testing are critical:
- Functional testing. Ensure that all features and functionalities work as intended. Test user registration, identity verification, and data management processes.
- Security testing. Perform vulnerability assessments, penetration testing, and code audits to identify and mitigate potential security risks.
- Performance testing. Evaluate system responsiveness, scalability, and resource consumption under various loads. This helps ensure the system can handle high user volumes.
- Usability testing. Collect feedback from users or testers to evaluate the system’s user-friendliness and identify areas for improvement in the user experience.
- Compatibility testing. Confirm that the system functions correctly on different devices, browsers, and operating systems.
- Data integrity testing. Verify the accuracy and consistency of data stored on the blockchain and associated databases.
- Load testing. Assess how the system performs under peak loads and ensure that it can handle a large number of concurrent users.
Once thorough testing in the staging environment has been completed, it’s time to deploy the system to the production environment.
Ongoing Maintenance and Support
Blockchain-based identity management system requires ongoing maintenance to succeed. Identifying and resolving software bugs is an ongoing process to maintain a reliable and secure identity management system. At the same time, adapting to changing user requirements and emerging technologies requires adding new features. This process entails:
- User needs assessment. Continuously gather user feedback and assess emerging needs to identify potential areas for improvement.
- Feature planning and development. Develop a roadmap for adding new features, prioritizing those that align with user needs and strategic objectives.
- Testing and QA. Rigorously test new features to ensure they function correctly and do not negatively impact existing system components.
Security enhancements are also critical to protect user data and maintain user trust.
Summary
By leveraging blockchain’s decentralized and secure nature, blockchain-based identity application development addresses many challenges, from reducing identity fraud to streamlining insurance processes, minimizing document forgery, and combating the spread of fake news on social media platforms.
With its potential to revolutionize multiple industries and facilitate cross-sector collaborations, blockchain-based identity application is a driving force behind global digitization. It can create a more secure and efficient digital environment.
Are you ready to be at the forefront of this digital revolution? Contact us at IdeaSoft right now! Together, we will build a future where secure, user-centric, and efficient digital identities become the new norm.